The term “attack path” often brings to mind memories of my time as Chief Marketing Officer for a breach simulation firm, where I learned of adversaries’ tactics commonly seen in traditional security evaluations. However, the ongoing convergence of traditional security methods with application security (AppSec) best practices is progressively obscuring the boundaries between the two domains. An approach gaining prominence in AppSec is attack path analysis. Yet the nuances of attack path analysis, its significance for software supply chain security, and the many considerations for adoption remain somewhat unkknown. Through this series, we aim to unpack what, why and how. Our initial piece will offer a basic overview while the next will delve into how attack path analysis can assist with reachability and exploitability evaluations.
What is attack path analysis?
Interestingly, when seeking to define attack path analysis, search results are flooded with blog posts from conventional security vendors providing overviews (and yes, I’m contributing to that influx, though let’s stay focused). However, Tech Target characterizes attack path analysis as “an approach that assesses the components, configurations, connections, and interactions within a given system that could enable a route by which aggressors could achieve their objective. By reproducing and visually portraying all possible pathways to key assets, the tool enables security teams to evaluate the potential risk, impact, and relationships between multiple attack scenarios and prioritize their mitigation efforts.” The same applies to application security, where some solutions focus on code, others on APIs, clouds, or an amalgamation thereof.
Why should you consider using attack path analysis?
There are great reasons why attach path analysis should be adopted. To some it may just feel like a visualization, but in reality it can turn knowledge into action and help team collaborate by showing the attack paths and the evidence behind critical vulnerabilities. This analysis helps in prioritizing security improvements by highlighting the most vulnerable and impactful routes, ensuring resources are allocated efficiently to where they are needed most. Other areas where it helps.
- Enhanced risk awareness: By providing a comprehensive view of their entire security posture, organizations can pinpoint potential vulnerabilities and routes of attack that could be exploited.
- Proactive threat prevention: Through proactively identifying weaknesses and anticipated paths of infiltration, companies can take preventative action to thwart possible dangers before they have an opportunity to materialize.
- Optimizing third party risk management: This analytical approach extends beyond a single entity by evaluating the security arrangements of providers and external services. Users are then capable of swiftly determining if they are at risk should an issue emerge with a third party.
- Adherence to compliance standards: It aids achieving compliance with constantly evolving regulations. Regulations may appear to change daily but their core principles endure. When vulnerabilities and their connections are illuminated, generating necessary reports is simplified.
- Enhanced incident response: Through attack path examination, security teams can develop more effective response plans in the event of a breach. This planning includes anticipating possible scenarios of infiltration and outlining proactive steps to curb impact.
- Refinement of security infrastructure: We often hear adding resources is not the sole solution. Insights from attack path analysis can be applied to redesign or strengthen an existing security framework, making it more resilient against potential threats.
How can attack path analysis be implemented in application security?
In AppSec, attack path analysis plays a critical role in identifying and mitigating risks associated with software vulnerabilities. It is crucial to consider not only code but also APIs and the cloud. Implementation involves:
- Identifying vulnerabilities: APA begins with pinpointing vulnerabilities within the application, including code flaws, misconfigurations, and dependencies with known security issues.
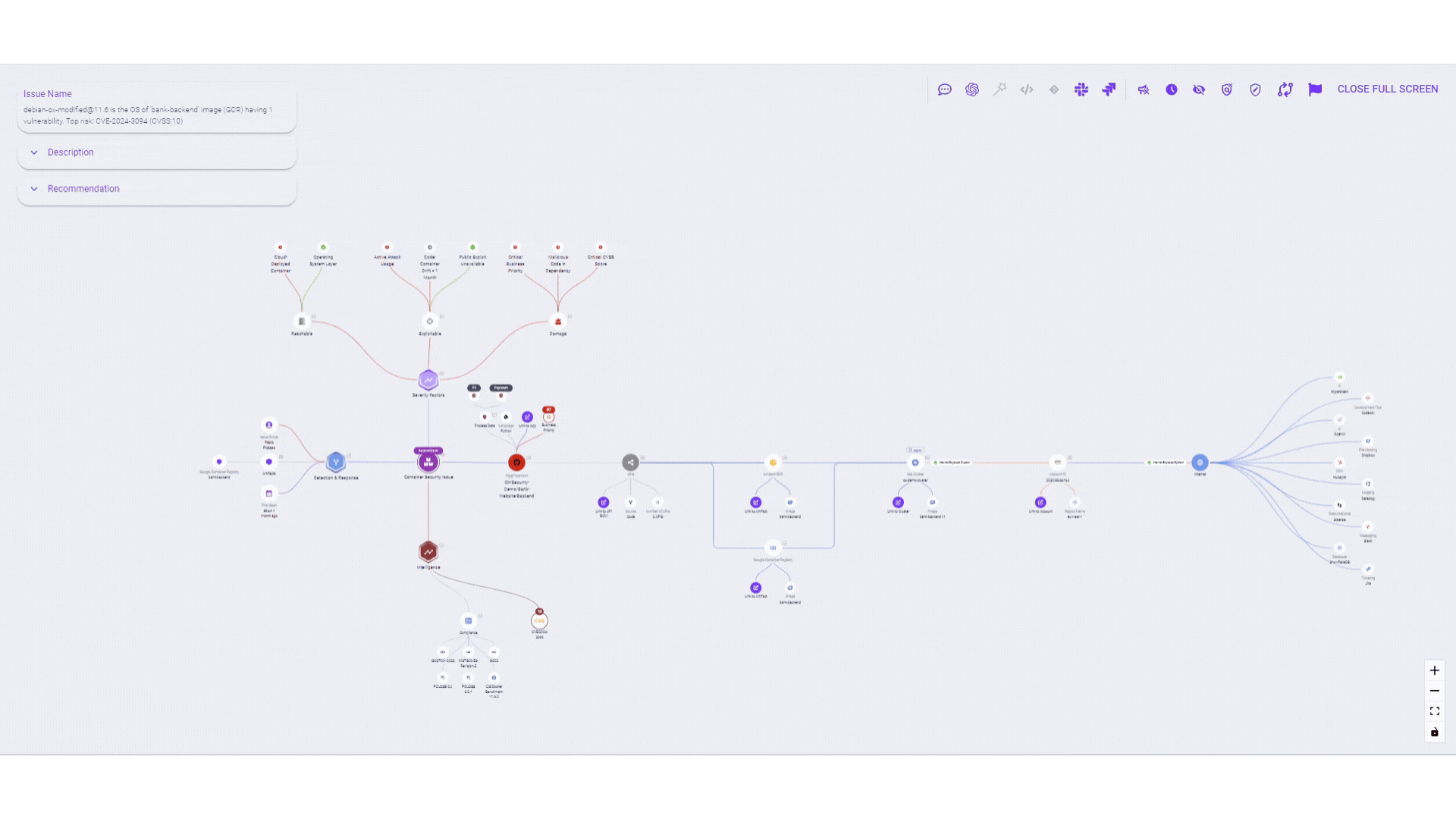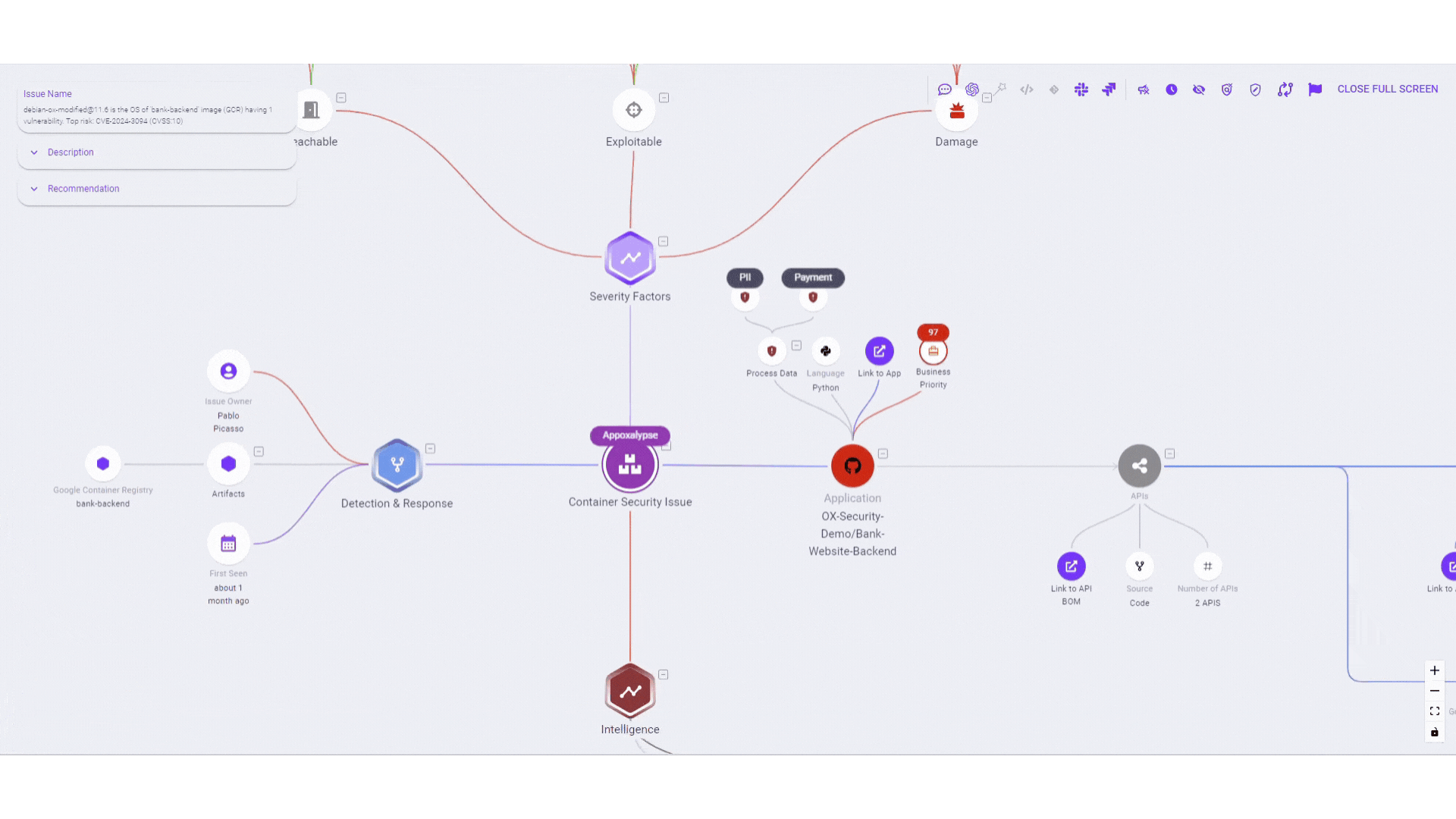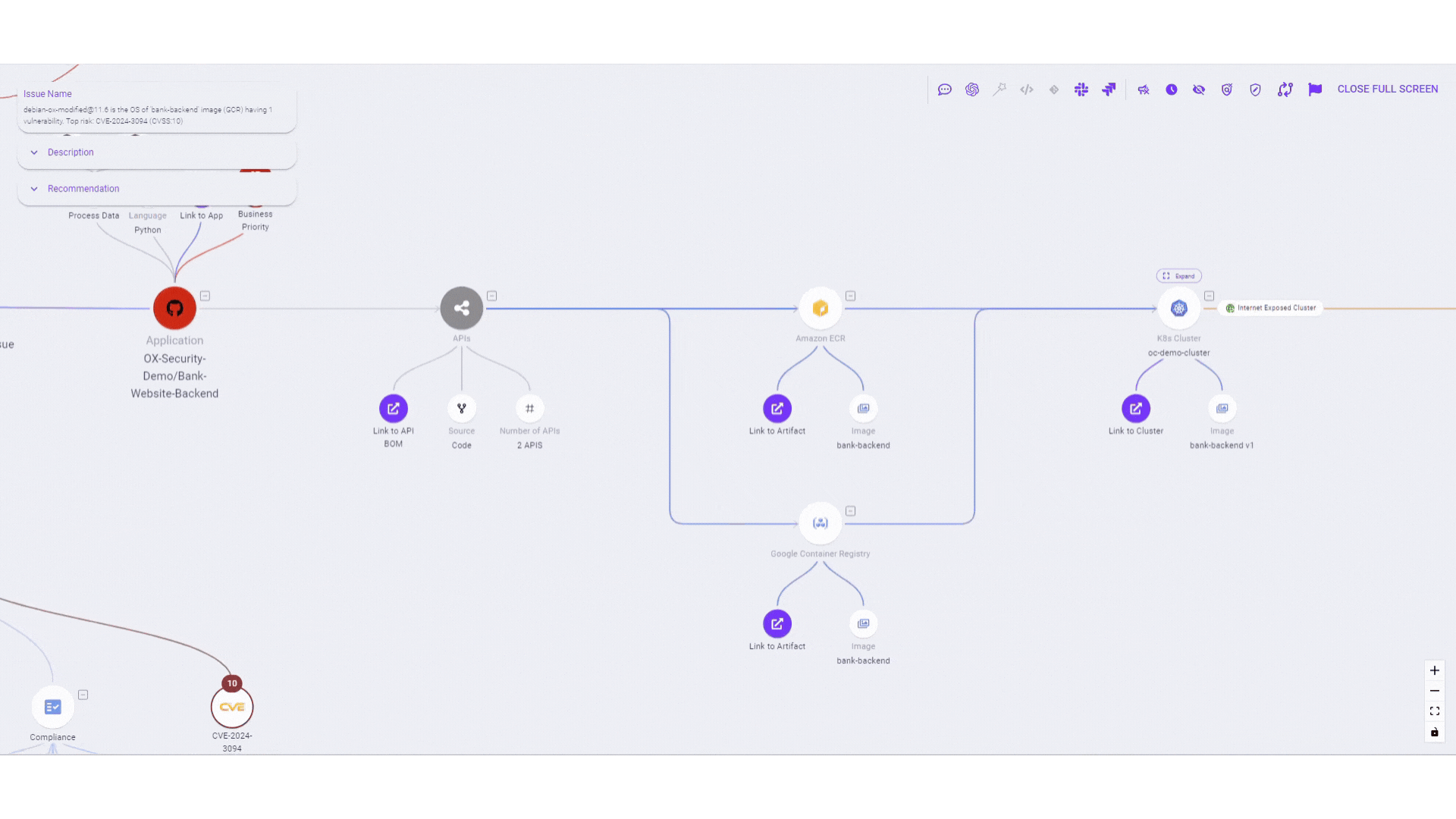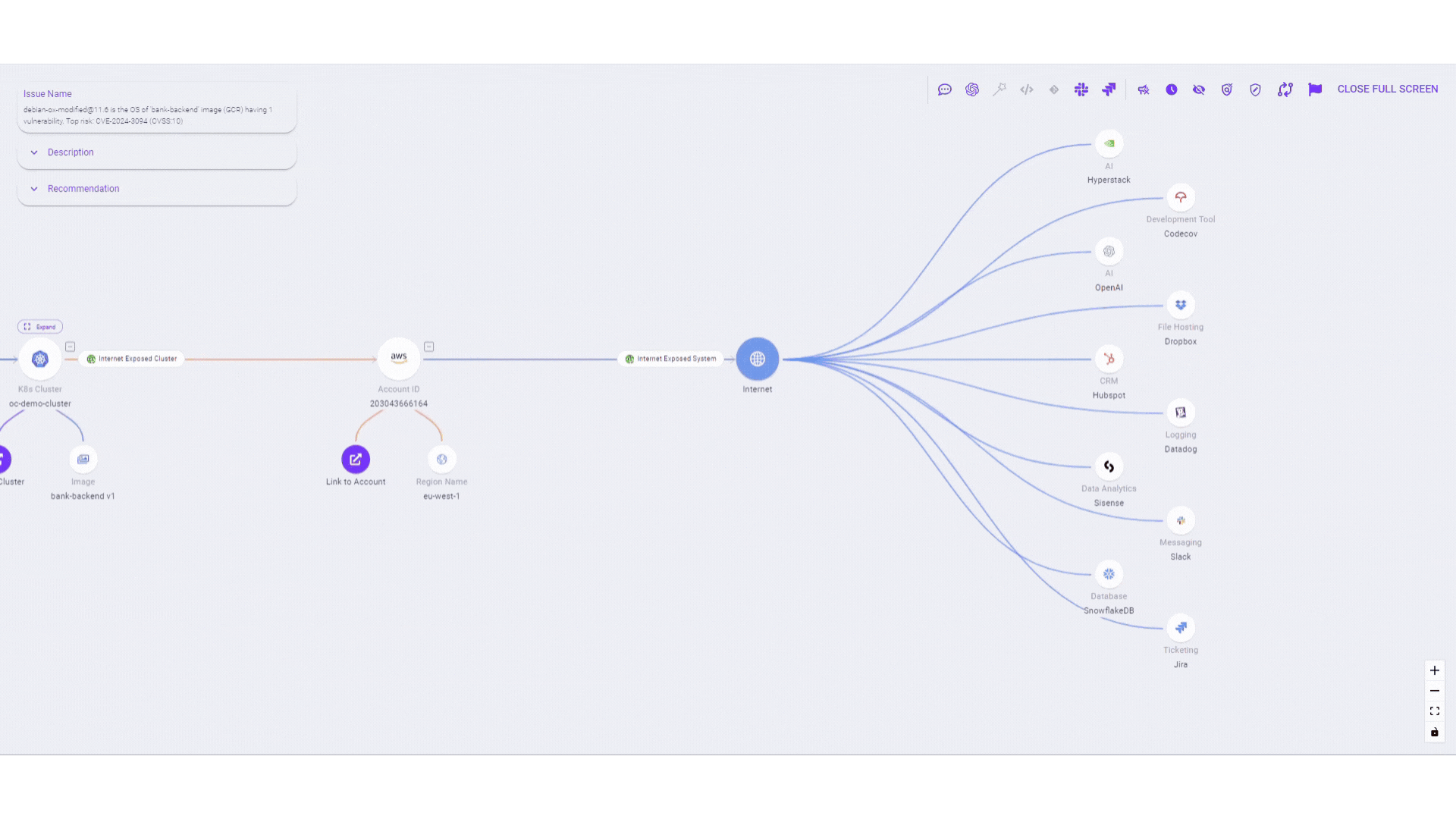
- Mapping attack paths: Once vulnerabilities are identified, attack path analysis maps out potential routes attackers could take to compromise the application, analyzing data flow, authentication mechanisms, and access controls.
- Prioritizing remediation: By understanding critical attack paths, organizations can prioritize remediation efforts based on potential impact and likelihood of exploitation.
- Continuous monitoring: Attack path analysis necessitates ongoing monitoring and updates as new vulnerabilities emerge or system architecture evolves.
Understanding reachability and exploitability
Although this is part of the how, reachability and exploitability deserves its own sections as Vendors often discuss reachability and exploitability, how crucial it is for comprehensive risk assessment. Merely having a list of vulnerabilities offers visibility, but you should be cautious with what you ask for. Long lists are not effective in eliminating risks; they are merely where you should start exploring potential risks. This is where reachability and exploitability come in.
- Identifying critical attack paths: Reachability analysis identifies potential pathways for attackers to reach critical assets, while exploitability assessment evaluates vulnerabilities along these paths to determine the likelihood of successful exploitation.
- Quantifying risk exposure: Reachability and exploitability together provide a holistic view of risk exposure, enabling organizations to prioritize mitigation strategies effectively.
- Optimizing resource allocation: By focusing on vulnerabilities that are both reachable and highly exploitable, organizations can allocate resources more efficiently, maximizing the impact of security investments.
Closing Thoughts
Over the next you will hear a lot about attack path analysis from us (we have a pretty amazing feature in our product), Seriously, implementation of attack path analysis offers a robust strategy to enhance our security posture. By understanding the nuances of attack path analysis organizations can better protect their critical assets from potential threats, ensuring a more secure and resilient software supply chain and products.
Stay tuned for more insights in the next part of our series, where we will delve deeper into practical applications and case studies around reachability. If you can’t wait until then our team is happy to show you a demo.