Last week, we announced several new releases that elevate our existing solution and create the OX Active ASPM platform. It’s no secret that speed, simplicity, and scalability are paramount to mitigate risk. Including OX Security’s Attack Path analysis in the platform represents a significant leap forward in enabling security and development teams to refine and enhance their risk mitigation strategies while taking steps to eliminate manual application security practices. I am proud to share this new feature crafted to streamline the comprehension and management of AppSec risk, offering a new lens through which it can be viewed and addressed, emphasizing the adage that “one picture is worth a thousand words.”
Empowering Quick and Informed Decisions
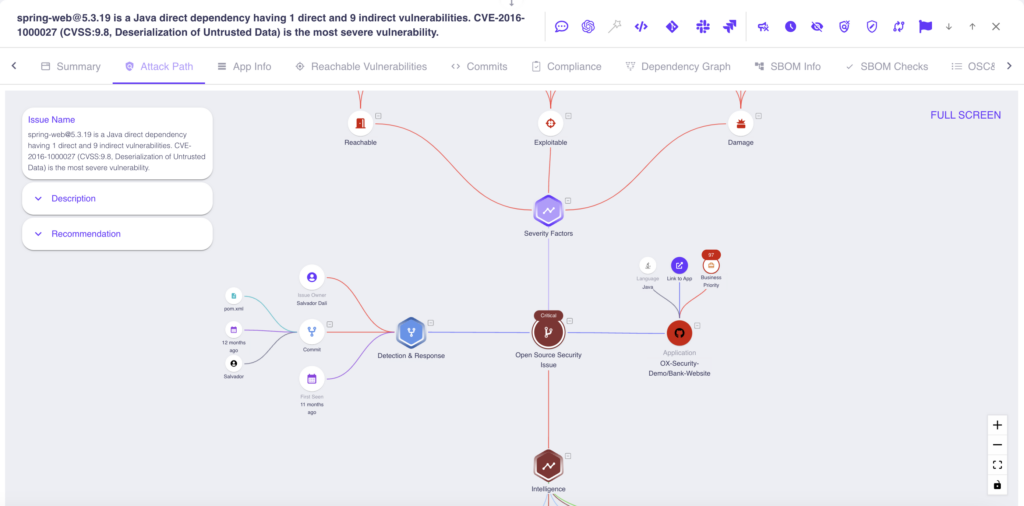
The essence of the Attack Path analysis lies in its ability to consolidate and clarify critical data. Presenting essential information about security issues through an intuitive visual format eliminates the cumbersome process of sifting through multiple tabs or documents. This visualization fosters a rapid comprehension of the nature and implications of risks, outlines recommended measures, and facilitates prompt action.
Key Enhancements Brought by the Attack Path Analysis
- Centralized information: The Attack Path analysis organizes data around focal points, simplifying the discovery and understanding of risks.
- Focused prioritization: Amidst abundant data, the graph highlights crucial issues, like severe vulnerabilities, ensuring attention is directed where it’s most needed.
- Contextualized application insights: The graph showcases critical information specific to the implicated application, including its business impact, aiding in making nuanced security decisions.
Streamlining AppSec Operations and Stakeholder Communication
The Attack Path analysis’s benefits extend beyond simplification, fundamentally helping organizations build cross-functional security engagement.
Streamlining Operations: It offers security teams a comprehensive analysis of each security challenge, merging key insights from severity evaluations, causative factors, and recent code changes to identified vulnerabilities. This holistic view not only informs but also equips teams with practical strategies for resolution. Integrating seamlessly with tools like Jira facilitates efficient remediation processes, from initiating pull requests to ticket generation, guiding every step with informed, strategic considerations.
Enhancing Engagement: The Attack Path analysis is also a critical bridge in communication with stakeholders. More than a mere informational tool, it acts as a lens through which the intricacies of security issues are made clear to a varied audience, including Developer Managers, Architects, and DevOps specialists. Transforming complex information into digestible insights fosters a shared understanding and promotes a proactive security culture across different expertise. In doing so, it advances discussions around security and sparks well-informed decisions, aligning diverse teams toward enhancing security frameworks and safeguarding digital infrastructures.
Beyond the Present: The Evolution of the Attack Path Analysis
The journey of the Attack Path analysis continues. Later this year, it will also include the identification and comprehension of security issues and enable the exploration of complex attack vectors visually. This capability promises to arm security teams with the foresight and tools necessary to fortify their defenses for preemptive action against vulnerabilities.
The Attack Path analysis is more than a visualization, it is the next step in our mission to eliminate manual AppSec. Providing a centralized, clear visualization of security challenges empowers you to act swiftly and with greater insight. Looking forward to its more profound development, we see a future where cybersecurity visualization encompasses a broader view and a deeper, actionable understanding, enhancing precision and strategic action in the digital security landscape.
See OX Attack Path Analysis for yourself: