Advanced Vulnerability Scanning for DevSecOps
Quickly detect, analyze, and fix known vulnerabilities in code and open-source dependencies before any web app has been compromised in just minutes with OX Security.
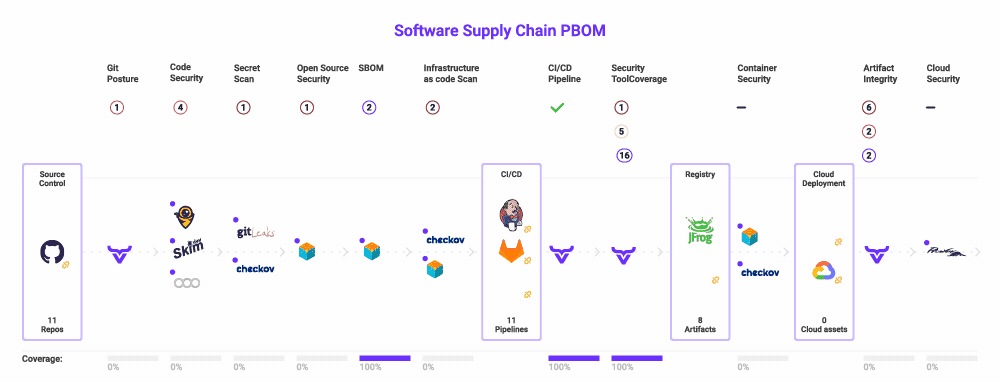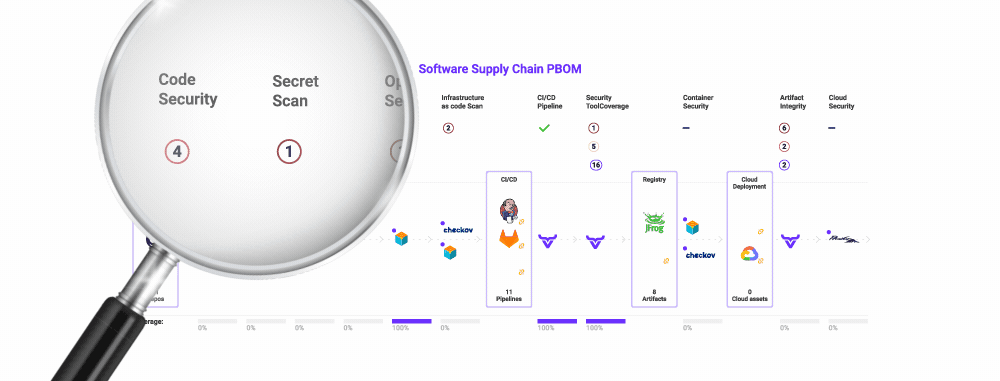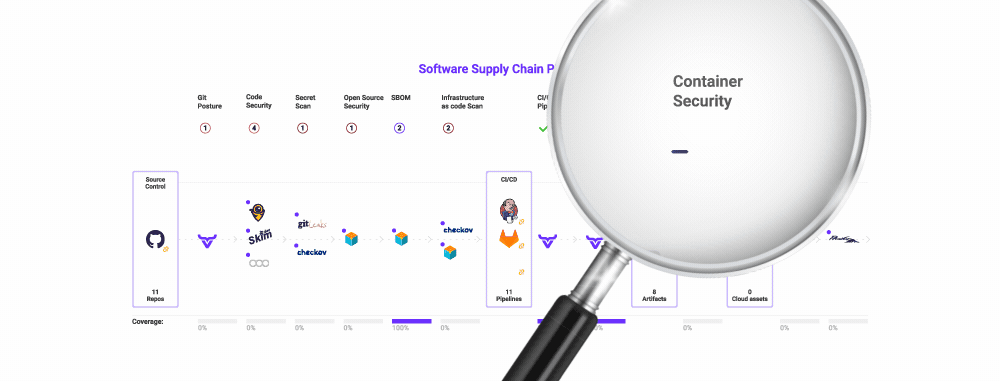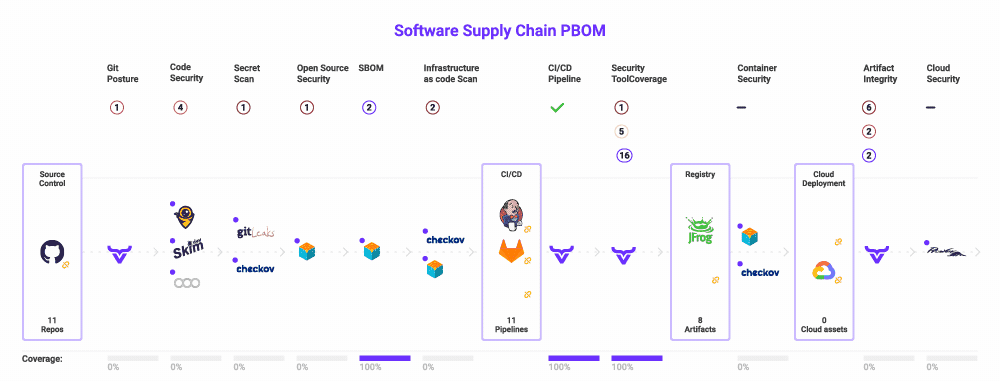
Quickly detect, analyze, and fix known vulnerabilities in code and open-source dependencies before any web app has been compromised in just minutes with OX Security.



Scan your entire SDLC

Prioritize with context


Mitigate risks faster
Scan your GitHub repositories for any branch protection that can be bypassed. Check for admins or third parties with too many permissions. Prevent unauthorized access to repositories and minimize the attack surface by assigning granular role-based permissions.
Gain complete visibility over your software supply chain from the first line of code to release. Reduce false positives with a built-in SAST tool baked into the security pipeline. Consolidate security findings into a single pane of glass without disrupting developer workflows.
OX’s end-to-end software supply chain security platform provides single-click integration with your existing CI/CD tools, such as Jenkins, CircleCI, GitLab CI, Bitbucket, and more.
Automate compliance validation and reporting throughout the DevSecOps lifecycle. Effortlessly pass audits with over 35 built-in security frameworks, such as ISO 27001 and SOC 2. Leverage best practices to identify risks in open-source components and ensure you meet all regulatory compliance requirements.
"OX is truly changing how companies secure their software supply chain, ensuring that all code comes from secure and trusted builds."
"OX is changing the software supply chain security game. It gives a complete and reliable snapshot of code security before development."
“OX brings back the much needed control enterprises have lost with the rapid shift to the cloud.”